Make an appearance Black Hat Asia 2023, 360 Publicly release research results on heavyweight vulnerabilities
recently, Black Hat Asia 2023 (Asian Black Hat Conference) Opening the curtain as scheduled in Singapore. As recognized as the highest event in the world's information security industry, Black Hat Every year, the latest safety research results are continuously transmitted to the outside world, Innovative technology and other cutting-edge information, It is the best window to showcase the trend of global security development.
since 2014 Starting from, 360 Has been on the board for ten consecutive years Black Hat The Stage of the Global Black Hat Conference, In this year's Black Hat Aisa At the conference, 360 Digital security Group was invited again, those under one's command 360 Security experts from the Vulnerability Research Institute announced, They developed a grammar variation based on syntax tree and context analysis Fuzz, In order to Chrome Find in WebSQL High risk vulnerabilities.
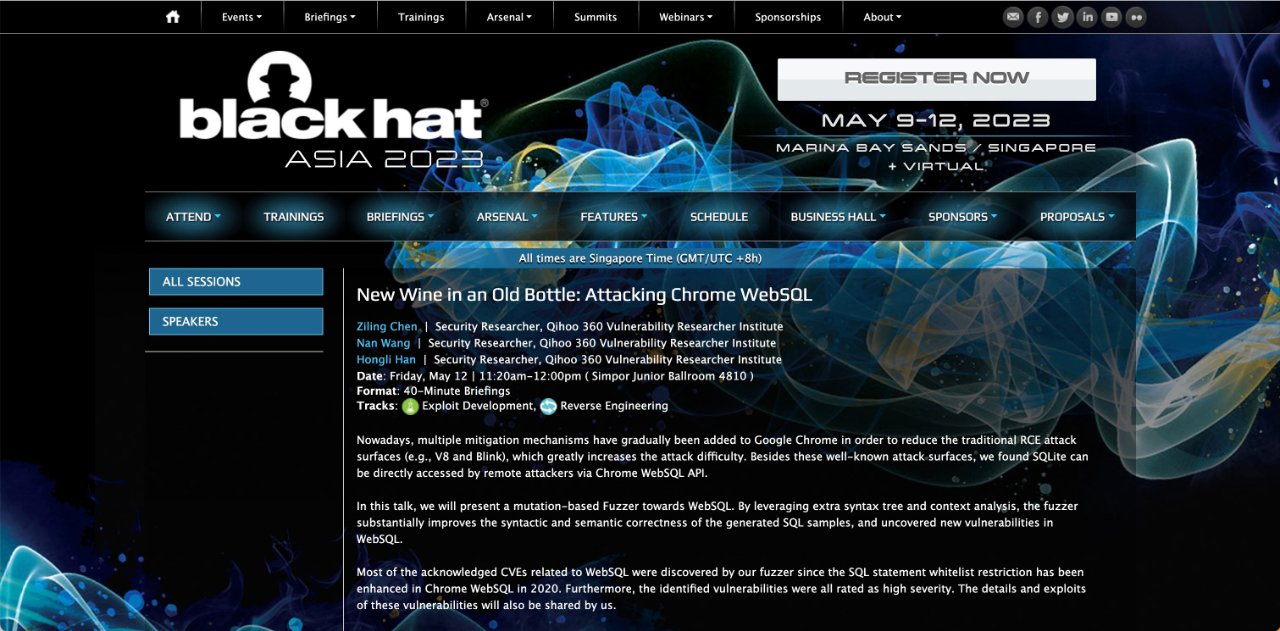
They expressed that: "along with Chrome Gradually adapting to tradition RCE Attack surface (V8 and Blink) Added mitigation mechanisms, Greatly increase the difficulty of the attack, Therefore, by WebSQL API By attacking the underlying layer SQLite Engine to attack Chrome Received our attention again. since 2020 Since the beginning of the year, ours Fuzzer Discovered the vast majority Chrome WebSQL loophole, Including multiple post release vulnerabilities, Stack overflow and out of bounds read and write vulnerabilities. "
In this speech, They provided a detailed introduction to the Fuzzer Working principle and advantages of, Including ensuring the validity of grammar by constructing a complete grammar tree, Guiding mutation strategies through contextual analysis, Achieve better semantic validity, And achieve better seed screening mechanism and coverage guided tree node mutation method.
although Chrome WebSQL The whitelist of has been enhanced, 2020 Years later Chrome In WebSQL Significant reduction in vulnerabilities, But the Fuzzer Continuously discovering new high-risk areas WebSQL loophole. These vulnerabilities may lead to arbitrary address reading, Impact of stack overflow and out of bounds writes, These vulnerabilities allow for complete control of memory layout, Hijacking some registers, Implement arbitrary address reading, Causing information leakage, It can even achieve remote code execution (RCE) .
They also emphasized that, SQLite stay Chrome Middle is an easily overlooked weakness, Introducing third-party libraries always comes with some security risks. The Fuzzer Can be improved SQL Fuzzer Grammatical and semantic validity of, To discover more SQLite loophole. They expressed that, The Fuzz The method is applicable to all grammar class targets, By constructing the required contextual analysis for different goals, You can use this set Fuzzer Apply to more platforms or targets.
In this year's Black Hat Asia in, 360 This highly valuable security achievement submitted by the Vulnerability Research Institute, Once again showcasing the flourishing pulse of China's security forces to the world. Prior to this, 360 The Vulnerability Research Institute has repeatedly shaken the world with its security capabilities, Not only becoming Microsoft MSRC, Tu Bang in international awards such as the Tianfu Cup "Frequent customers" , Also honored as China's first "The Pwnie Awards" Epic level achievement award and best empowerment loophole award, And it has been awarded the annual report of Google's official vulnerability reward program for many consecutive years (VRP) Public thanks.
-
Classification of this article: Company News
-
Article label:
-
Number of views: 5167 Views
-
Release date: 2023-05-19 11: 44: 29
-
Link to this article: https: //www. fangcloud. com/cms/gsxw/775. html
Popular recommendations
- 360 Fangcloud助力 500 强企业晶科能源实现多地高效协同
- 360 告警: 全球知名大模型框架被曝loophole! 或致 AI 设备集体失控
- 入选领域最多, 影响力最广泛! 360 上榜 2024 网络安全十大创新方向
- 360 Fangcloud AI 增值服务上线, 超大限时优惠等你来!
- 华诺科技与 360 FangcloudAchieving strategic cooperation, 共推 AI 大模型产业化落地
- 央企控股上市公司引入 360 FangCloud Enterprise Online Disk, 搭建智慧协同云平台
- 美容品牌「御研堂」引入 360 Fangcloud, 高效管理whole country近百门店
- 天津医科university总医院: 借助 360 Fangcloud实现文件安全管理
- 助力数字化-型, 3 制造企业通过 360 Fangcloud高效协同办公
- in国人民university, in国科学院university等众多客户签约 360 Fangcloud
最新推荐
- 航空 AI 白皮书发布, 重塑航空未来, 让知识成为生产力
- 360 Fangcloud×DeepSeek-R1 满血版, 提效新选择, 免费领取会员权益!
- 入选领域最多, 影响力最广泛! 360 上榜 2024 网络安全十大创新方向
- 数字政府新标杆! 朝阳 "City 不 City 啊" ?
- 360 携 20+ "终端能力者" ! 组建 ISC 终端安全生态联盟
- 360 告警: 全球知名大模型框架被曝loophole! 或致 AI 设备集体失控
- 人们, 咱安全圈可不兴 "没苦硬吃" !
- 黑神话: 悟空 疯狂 24 小时: 爆火下的网络安全陷阱
- 攻防演练实录 | 360 安全大模型再狙 0day loophole, 助蓝队 "上大分" !
- Gartner 最新报告! 360 "明星Products" 搭载安全大模型战力领跑市场

 400-993-9050
400-993-9050










 浙公网安备 33011002015048 号
浙公网安备 33011002015048 号 Wechat Consulting
Wechat Consulting
 Phone consultation
Phone consultation