Zhejiang Bulletin 6 Wechat office leak cases, How to ensure information security in the era of Collaborative Office?
The popularity of the Internet makes people's work and life more and more convenient, Enterprise employees, The staff of organs and units are also getting used to it "Handy" Use wechat, QQ And other social tools, But this brings great challenges to confidentiality.
Just a few days ago, Zhejiang Province reported 6 rise 2022 Typical cases of wechat leaks in the first half of, The subject involves government departments and units, bank, colleges and universities, Enterprises, etc, Several public officials involved used wechat transmission in violation of regulations, Criticized for handling classified office documents, punishment, Attract attention from many parties.

(Quoted from official account [Zhejiang Today ] )
We can see, The most common violations in the above cases mainly include:
"
1
Take photos of confidential documents at work, Wechat forwarding to colleagues/friend/Wechat group;
Take photos of classified documents, Use wechat to recognize words in photos, Save to your phone or computer, Convenient for subsequent office work;
2
"
"
3
Illegal downloading of classified documents, Forward to wechat group to share with colleagues.
This involves 4 Class unsafe factors, Each category is very easy to cause sensitive information disclosure:
1
Unsafe office environment (Social environments such as wechat) ;
2
Unsafe office equipment (For example, own computer, Own mobile phone) ;
3
Lack of personnel authority control mechanism (For example, anyone can download, Forward file) ;
4
Lack of behavior control mechanism (For example, documents can be easily photographed, Screenshot, copy, Download, etc) .
As netizens commented, Information confidentiality is a 100-1=0 Problems of, One mistake may lead to a complete recovery 0.
And wechat, QQ And other instant messaging tools, Social attributes, Once the sensitive working documents are mixed into it, It is bound to be difficult to prevent information security risks.
This reminds us again:
Government affairs requiring information confidentiality, business organization, Need to further enhance the awareness of confidentiality, Build an independent collaborative office platform, Avoid using social tools such as wechat to publish, transmission, Processing working documents, Strictly ensure the security of confidential documents.
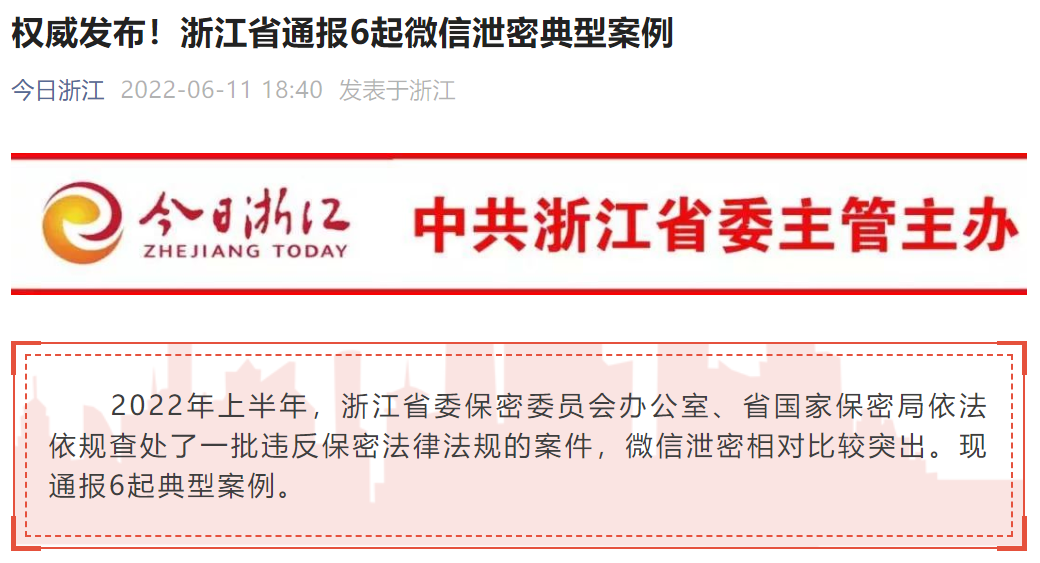
As 360 Wholly owned subsidiary of the group, 360FangcloudAbsorbed 360 The group has advanced security technology and rich user service experience in government and enterprises, Deeply integrate it into collaborative office products;
It is a government agency unit, bank, colleges and universities, Construction of enterprises and other customerscomprehensive (Local file+Cloud files+Outgoing documents) Content level document security control system, as well asWhole process (Precaution in advance+In process control+Prevention after the event) Document safety protection system;
comprehensive, Full link, Ensure the security of file data in the whole life cycle of users' collaborative office without dead ends.
that, How can users use 360FangcloudImplement security, Efficient collaborative office?
(1) Build a collaborative office platform
360 Yifang cloud builds an unstructured data platform for users, All types of office documents can be securely stored inCloud diskin.
It can be easily achieved among colleaguesFile sharing, Online collaborative office (for exampleMulti person online editing at the same time, Document comments, File sharing) etc, No longer need to use wechat, QQ And other social software transmission, Processing office documents.
(2) Refined personnel authority control
360 Yifang cloud has8 Level authority control system, Enterprises and institutions can set different permissions for each staff member, for example, Confidential documents can only be accessed by those with permission, operation, Unauthorized persons cannot access confidential documents.

(Refined authority control system)
(3) Cloud file security control
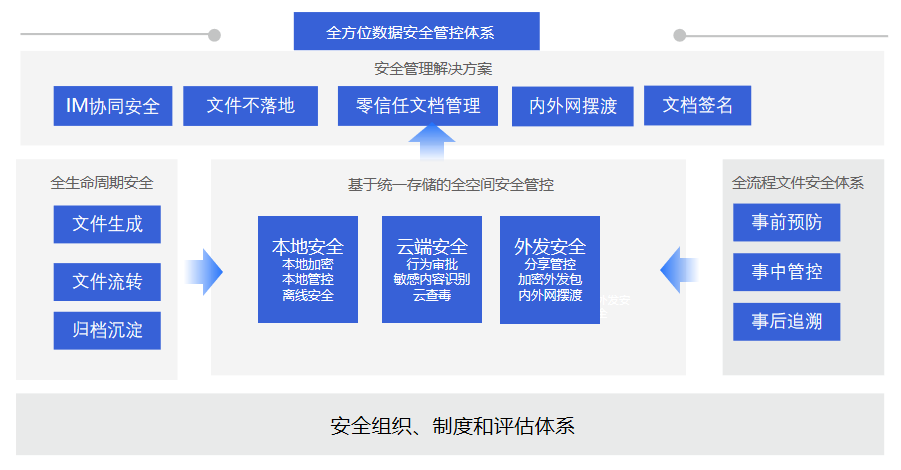
Anti virus and anti accidental deletion, Eliminate data loss
If the internal personnel of the enterprise are not careful (Or intentionally) Upload infected files to the enterprise database, It will cause the spread of virus files.
If the document is accidentally deleted or modified by the employee, And the file of the previous version cannot be retrieved, Data assets will be lost.
In order to defend against these risks, 360 Yifang cloud passesPrecaution in advance, In process control, Trace the three lines of defense afterwards, Eliminate virus infection in enterprise databases, Prevent data loss.
(Antivirus, Loss prevention scheme)
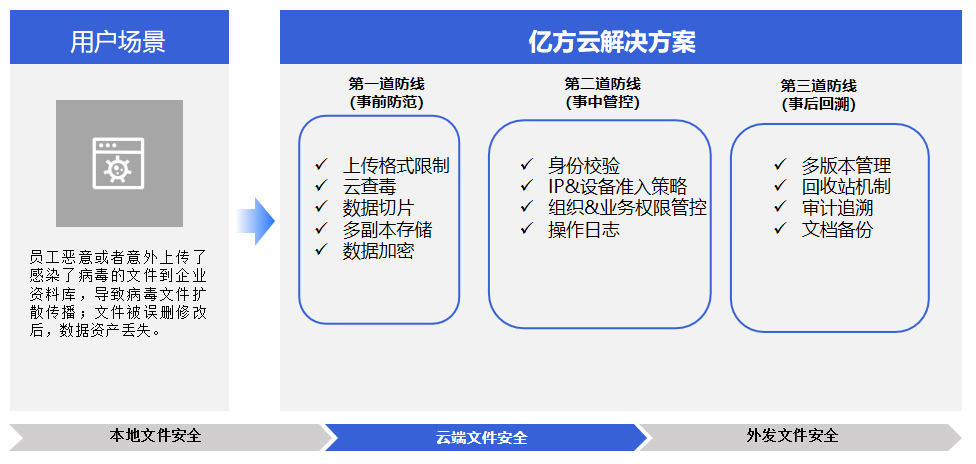
behavior control , Prevent internal personnel from divulging Secrets
360 Yifang Cloud's impact on enterprise storageCloud diskSet security protection mechanism for files in.
for exampleConfidential documents can be previewed online by employees with their personal watermarks, Online editing, And employees move their positions, copy, Downloads, Share and other sensitive operations, Approval will be automatically triggered, Only after being approved by the superior, Before relevant operations can be carried out.
(Cloud file behavior control scheme)
thus, People inside the enterprise will have no chance to copy/Screenshot/Downloads/Disclose the important data stored in the cloud disk of the enterprise by sending it out.
Automatic detection and isolation of sensitive content
If some sensitive documents that cannot be uploaded to the database appear in them, It will bring compliance and audit risks to enterprises and institutions.
Enterprises and institutions canSet sensitive thesaurus in cloud disk, Automatic scanning when uploading files to cloud disk, Users can also identify the content of the entire cloud disk, Lock sensitive files when they are found, quarantine, Delete, etc, Ensure Non-Proliferation of sensitive information.
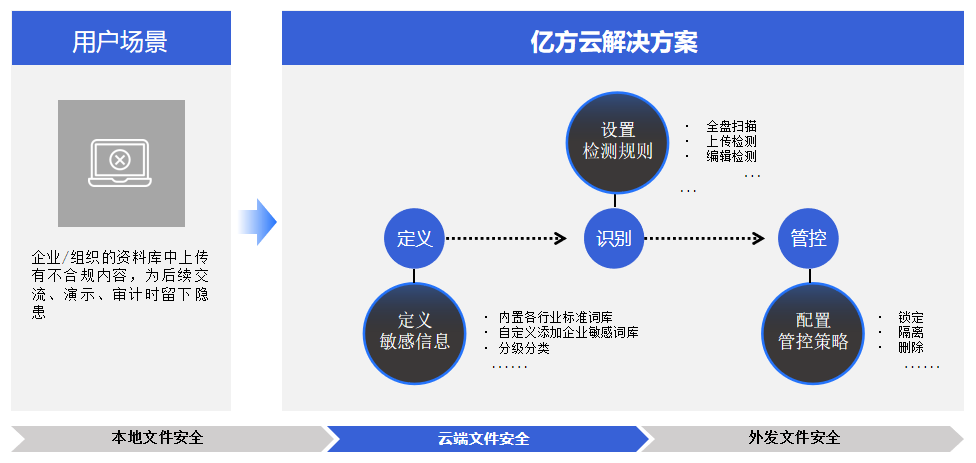
(Sensitive word recognition)
(4) Local document security control
File landing automatic encryption
In order to avoid employees downloading important documents of the enterprise to their computers, adopt U Disk copy take away, Or upload these materials to individualsNetdiskTake away in the middle.
360 FangcloudEnterprise cloud diskIt can automatically encrypt important files and data once they are landed.
Even if employees have permission to synchronize confidential documents, Download to the office computer equipped by the company, You can only open files and edit them locally through the specified client, Otherwise, it will be in ciphertext status, Unable to view and operate.
When an employee opens a file on his / her own computer after leaving the company, it is also classified as ciphertext, Unable to view and operate.
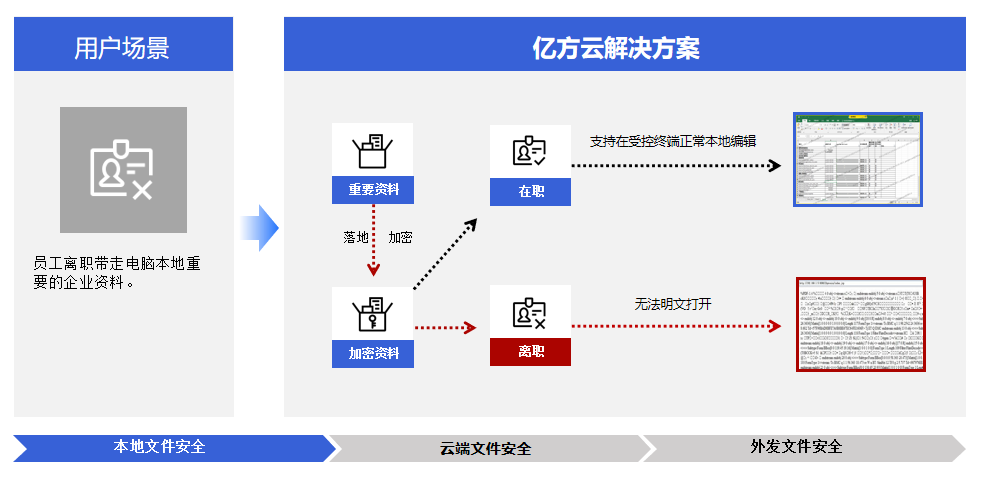
(File landing automatic encryption)
Terminal behavior control+File content protection
The employee opens a file that has been synchronized to the local computer, Employees' personal watermarks will still be attached to the screen, Deterrence against photographing and other behaviors, It is also convenient for later behavior tracing; just so soDisable screenshots of documents, Prohibit printing, Copying is only allowed within this document, Prohibit A Copy the contents of the document to B Documents, etc.
So as to avoid internal personnel from disclosing local documents, Selling the core secrets of the enterprise for personal gain.
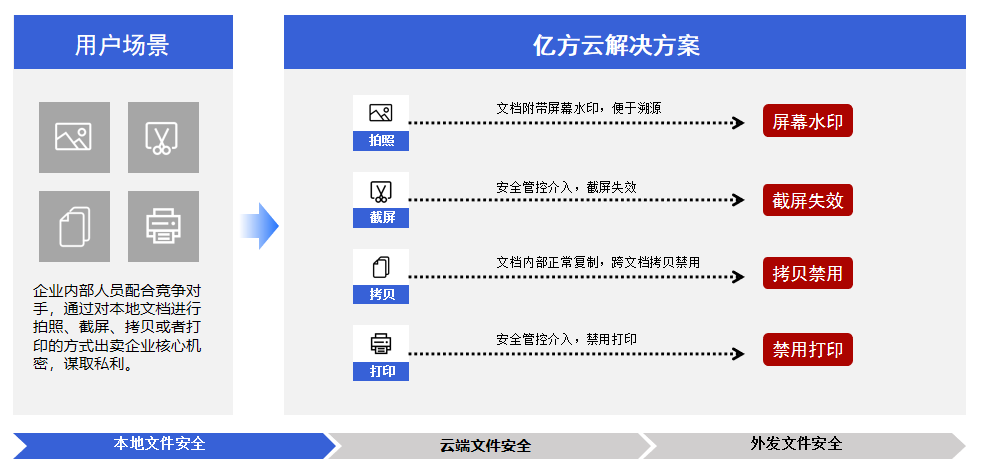
(Local document behavior control scheme)
(5) Whole process operation log supervision
stay 360 Yifang cloud, All operations of each employee have an operation log, Facilitate regular audits, Back at any time, If illegal operations are found, they can be stopped and dealt with immediately.

-
Article classification: Industry information
-
Article label:
-
Number of views: 2648 Browse times
-
Release date: 2022-06-16 17: 57: 41
-
Article link: https: //www. fangcloud. com/cms/hyzx/529. html
Popular recommendations
- 360 Yifang cloud assistance 500 Strengthening enterprise Jingke energy to realize multi place efficient collaboration
- 360 Fangcloud AI 增值服务上线, 超大限时优惠etc你来!
- 华诺科技与 360 Fangcloud达成战略合作, 共推 AI 大模型产业化落地
- Beauty brand「Imperial Research Hall」introduce 360 Fangcloud, Efficient management of nearly 100 stores nationwide
- 天津医科university总医院: 借助 360 Fangcloud实现文件securityAdministration
- Introduction of listed companies controlled by central enterprises 360 FangCloud Enterprise Online Disk, Build a smart collaborative cloud platform
- Facilitate digital transformation, 3 Manufacturing enterprises 360 Yifang Cloud efficient collaborative office
- in国人民university, in国科学院universityetc众多客户签约 360 Fangcloud
- 物产in大化工集团: 借助 360 FangcloudsecurityAdministration文档, higheffect协作to work in an office
- 深耕 "人工智能security" 三六零获评 2023 year北京 "隐形冠军" enterprise
最新推荐
- 入选领域最多, 影响力最广泛! 360 上榜 2024 网络security十大创新方向
- 数字政府新标杆! 朝阳 "City 不 City 啊" ?
- 360 携 20+ "终端能力者" ! 组建 ISC 终端security生态联盟
- 360 告警: 全球知名大模型框架被曝漏洞! 或致 AI 设备集体失控
- 人们, 咱security圈可不兴 "没苦硬吃" !
- 黑神话: 悟空 疯狂 24 小时: 爆火下的网络security陷阱
- 攻防演练实录 | 360 security大模型再狙 0day 漏洞, 助蓝队 "上大分" !
- Gartner 最新报告! 360 "明星Products" 搭载security大模型战力领跑市场
- 第五辆! 周鸿祎提车 "奇瑞星纪元" 持续为国产新能源车助威
- 重磅! 360 智能化数据security系列Products发布 实现数据可见, 可管, 可用!

 400-993-9050
400-993-9050











 浙公网安备 33011002015048 号
浙公网安备 33011002015048 号 Wechat Consulting
Wechat Consulting
 Phone consultation
Phone consultation